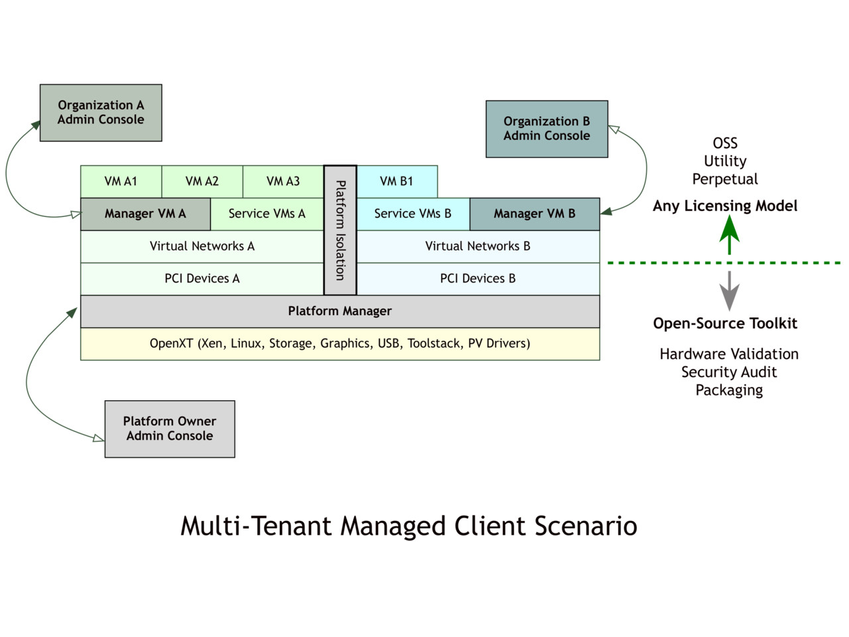
What is OpenXT?*
OpenXT is an open-source development toolkit for hardware-assisted security research and appliance integration. Released as Open-Source Software (OSS) in June 2014, OpenXT stands on the shoulders of Xen Project and OpenEmbedded. It is derived from XenClient XT, which was first released in May 2011. It includes hardened Xen VMs that can be configured as a user-facing virtualization appliance, for client devices with Linux and/or Windows guests. It has been used to develop managed software appliances to isolate demanding graphics workloads, untrusted workloads and multiple networks on a single laptop or desktop. OpenXT is optimized for x86 devices with Intel VT-d, TXT (Trusted Execution Technology) and a TPM.
OpenXT is being developed to meet the varied needs of the security and virtualization communities, as a toolkit for the configurable disaggregation of operating systems and user workflows. Client appliances developed on OpenXT can contain a mixture of open-source and proprietary software, supporting a range of business models.
History
2014
LinuxCon NA, Security in the Cloud: Xen, KVM, Containers, George Dunlap
Xen Summit, Security and the Properties of a Xen Virtualization Platform, Philip Tricca
2013
LinuxCon EU, Securing your cloud with Xen’s advanced security features, George Dunlap (video)
Xen Summit, In-Guest Mechanisms to Strengthen Guest Separation, Philip Tricca
Xen Summit, Secure Server Project, Jason Sonnek (video)
Multi-Level (MLS) Hypervisor for Server
2012
- Xen Summit, μ-Xen, Ian Pratt
Micro-Virtualization, Type-2 Hypervisor, VM Fork, Deprivileged Windows Host
- Xen Summit, Xen and Client Virtualization: the case of XenClient XT, Gianluca Guida
Client Virtualization, VPN VM, Linux Stub Domains, Graphics Virtualization, Inter-VM Communication, SE Linux, Xen Security Modules (XSM), Dynamic Root of Trust Measurement (DRTM), Service VMs, Intel VT-d, Intel TXT.
2010
- Qubes OS Architecture, Joanna Rutkowska
Secure GUI, Secure networking, Secure storage, Analysis of potential attack vectors
2007
- Xen Summit, Trusted Boot: Verifying the Xen Launch, Joseph Cihula
Research
2011
- ACM Symposium on Operating Systems Principles, Breaking Up is Hard to Do: Security and Functionality in a Commodity Hypervisor, Patrick Colp et al.
“We present Xoar, a modified version of Xen that retrofits the modularity and isolation principles used in microkernels onto a mature virtualization platform. Xoar breaks the control VM into single-purpose components called service VMs. We show that this componentized abstraction brings a number of benefits: sharing of service components by guests is configurable and auditable, making exposure to risk explicit, and access to the hypervisor is restricted to the least privilege required for each component.”
2008
- ACM Conference on Virtual Execution Environments, Improving Xen Security through Disaggregation, Derek Murray et al.
“We introduce our work to disaggregate the management virtual machine in a Xen-based system … moves the domain builder, the most important privileged component, into a minimal trusted compartment. We illustrate how this approach may be used to implement “trusted virtualisation” and improve the security of virtual TPM implementations.
2007
- ACM Workshop on New Security Paradigms, Robustly Secure Computer Systems: A new security paradigm of system discontinuity, Jon A. Solworth
2006
- Computer magazine, Can We Make Operating Systems Reliable and Secure?, Andrew S. Tanenbaum et al.
- USENIX Security, Virtualizing the Trusted Platform Module, Stefan Berger et al.
2003
- ACM Symposium on Operating Systems Principles, Xen and the Art of Virtualization, Paul Barham et al.
“This paper presents Xen, an x86 virtual machine monitor which allows multiple commodity operating systems to share conventional hardware in a safe and resource managed fashion, but without sacricing either performance or functionality.”
1998
- USENIX Security, The Flask Security Architecture: System Support for Diverse Security Policies, Ray Spencer et al.
1981
- IBM Journal of Research & Development, The Origin of the VM/370 Time-sharing System, R.J. Creasy
*This content is from openxt.org and is being used to support a proof of concept documentation effort for OpenXT.